So why would you bother use them? For the quality of the deployment (QOD? :-). By logically segmenting the voice and data worlds disruptions in either world will not affect each other (hopefully). You can firewall or use access lists between VLANs to help secure your VoIP deployment. Also, if you want DHCP / DNS to work differently for the phone system it doesn’t affect the data network.
I’m not going to get into the intricacies of VLANs here. Here’s the wikipedia entry (http://en.wikipedia.org/wiki/Vlan) which will help a bit. Get a couple of switches that support VLANs and play with them a bit… learn how to trunk VLANs between switches and how to statically map ports into VLANs. Learn them, live them, love them… you’ll use them all of the time.
On most VoIP deployments I’ll use 3 VLANs at a minimum. Data, Phone and Management. Data is the default VLAN and used for all PC’s, servers & printers. Phone is for all phones, gateways & PBX equipment. Management is for switch / router management IP’s.
Here’s what the VLAN diagram would look like:
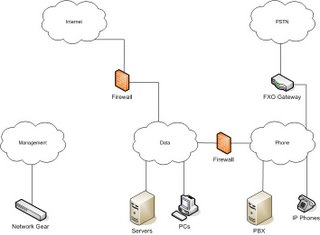
Statically map the PBX and gateway ports into the Phone VLAN. Setup all of the ports that will connect to PC’s and phones with the Data VLAN as the default VLAN (untagged) and the Phone VLAN as a tagged VLAN. That means that devices ‘tagging’ their traffic for the Phone VLAN will be placed in that VLAN and devices that don’t know how to tag their traffic will be in the Data VLAN.
Manually set your IP phones to be in the Phone VLAN. This means the phone will tag it’s traffic for that VLAN and pick up DHCP from that VLAN. It is possible for some phones to pick this up off of the initial DHCP reply to the phone and then switch to the Phone VLAN and get another DHCP address from that VLAN. However, now you are depending on the DHCP server on the Data VLAN to be working.
No comments:
Post a Comment